By Duane Wilson
SURVIVABILITY BACKGROUND
In the military environment, survivability is defined as the ability to remain mission capable after a single engagement. Engineers working in survivability are often responsible for improving four main system elements [1]:
- Detectability – the inability to avoid being aurally and visually detected as well as detected by radar (by an observer).
- Susceptibility – the inability to avoid being hit (by a weapon).
- Vulnerability – the inability to withstand the hit.
- Recoverability – longer-term, post-hit effects, damage control, and firefighting, capability restoration, or escape and evacuation.
- These elements cover the gamut of potential issues that could be experienced during the course of any mission. In this article, we aim to draw a conclusive parallel with cybersecurity that can leverage these principles as it relates to mission systems. In short, cybersecurity still focuses on pre- and post-attack defensive techniques that have proven to be ineffective given the proliferation and increase of cyberattacks.
CYBERSECURITY EVOLUTION
The advent of cybersecurity is often attributed to the first major computer virus—the Morris Worm of November 2, 1988 [2]. Although, the first recorded computer virus Creeper was developed in 1971 by Bob Thomas at BBN Technologies [3], it preceded the modern-day Internet; hence, it did not have as great of an “impact.” The Morris Worm was designed by Robert Morris as an exploratory to understand the “vastness” of the Internet. Within 24 hr, ~6,000 of the 60K computers (10%) then connected to the Internet had been infected by the worm. The worm only targeted computers running a specific version of the Unix operating system, but it spread widely because it featured multiple vectors of attack. For example, it exploited a backdoor in the Internet’s electronic mail system and a bug in the “finger” program that identified network users. It was also designed to stay hidden [2], making it difficult to eradicate.
In response to this attack and many others since then, the cyber community has responded in several ways to mitigate the potential for these types of attacks in the future. These response actions largely fall into the following categories: compliance, intrusion detection, software patching, digital forensics, and defense in depth. These categories are all designed to enable the six cybersecurity tenets—confidentiality, integrity, availability, authorization, authentication, and non-repudiation.
Confidentiality focuses on protecting the privacy of information from unauthorized disclosure and is largely accomplished through modern-day encryption. Integrity is simply your confidence in data. Can you trust it from source to destination? Availability is critical in the e-commerce space as it refers to the principle of ensuring that a resource is available to legitimate users. The emphasis is on uptime—how often is it unavailable vs. available. Authentication and authorization go together in that authentication proves someone is who they say they are while authorization proves that someone has the right to access a particular resource. Lastly, non-repudiation ensures that someone cannot deny that something happened or did not happen. For example, non-repudiation is very useful in email correspondence. Imagine if someone were able to deny they sent emails. This would cause a number of issues.
Compliance activities seeks to address security issues early in the system development life cycle. There are a number of compliance standards (e.g., National Institute of Standards and Technology Risk Management Framework) whose discussions fall outside this article, but their focus is on initial security and not continuous security. Intrusion detection picks up where compliance ends and offers various methodologies to respond to security incidents as they occur. It typically falls into two subcategories—signature-based and anomaly-based intrusion detection. Software patching is a well-known concept that complements compliance by addressing issues that occur after software has been written and put into production. Digital forensics is applied once an attack has occurred. It focuses on determining the who, why, what, where, and how of a cyberattack and is mainly used for attribution. Defense in depth is more of a conceptual framework that emphasizes layers of defense—assuming one or more will always fail. This is a great complement to the concept of cyber survivability.
CYBERSECURITY STATISTICS AND ARTIFICIAL INTELLIGENCE (AI)
With all of these great cyber constructs in place, should we all just pack up and quit our cybersecurity jobs and find new careers? Unfortunately, no. The following recent statistics from Norton Corporation, one of the preeminent providers of security products on the market [4], explain why:
- Cyber criminals land on FBI’s most wanted list.
- Mobile malware is on the rise.
- Third-party app stores host most mobile malware.
- Identity theft impacts 60 million Americans.
- Internet of Things devices can increase security vulnerabilities.
- Average cost of a data breach rises (e.g., impact on business operations).
- The U.S. government will spend $15 billion on cybersecurity.
- The United States is the no. 1 target for cyberattacks.
- The United States will account for half of breached data by 2023.
These are just a few of the recent trends in 2019 that indicate that we are still very much behind the adversarial community as it relates to defending against the latest and greatest cyberattacks or variations thereof. Additionally, there is also a sizable shortage of professionals equipped to respond to cyberthreats. A recent study by ISC [2], a nonprofit cybersecurity professional association, estimates that the industry is lacking close to 3 million workers across the globe [5]. Some companies have tried to fill the gap with AI and machine learning, but those technologies are in a nascent stage and will not address the larger problem.
AI is a superset of several areas and routinely used in cybersecurity for the following purposes [6]:
- Pattern recognition — identifying phishing emails based on content or sender info, identifying malware, etc.
- Anomaly detection — spotting unusual activity, data, or processes (e.g., fraud detection for online banking or gambling).
- Natural language processing (NLP) — converting unstructured text such as a webpage into structured intelligence.
- Predictive analytics — processing data and identifying patterns in order to make predictions and identify outliers.
It is often confused with machine learning, which refers to machines which “learn” while processing large quantities of data, enabling them to make predictions and identify anomalies [6]. Machine learning is the application of an AI principle. Specifically, AI encompasses any case where a machine is designed to complete tasks which, if done by a human, would require intelligence.
CHALLENGES WITH EXISTING APPROACHES
The AI revolution has never been about replacing humans with machines but about machines providing humans with the context and information they need to make informed decisions [6]. The focus of all of the aforementioned approaches was never to solve all cybersecurity issues. The following are some of the major challenges with existing approaches.
- Compliance – usually focuses on checking security boxes ONE TIME for the purpose of preparing for an audit, connecting to a network, or running on a system.
- Intrusion Detection – with signature-based approaches, it only works AFTER an attack has occurred at least once; with anomaly-based approaches, it requires an ACCURATE baseline of normal traffic, which is challenging in cyber-contested environments.
- Patching – does not prevent against Zero-Day attacks since it is largely a process that reacts to vulnerabilities identified by the community.
- Digital Forensics – although a very effective process, digital forensics focuses on the what, where, why, when, and how surrounding cyberattacks that have already occurred.
- Defense in Depth – aim of defense in depth is to prevent attacks from penetrating a system at each level of the “computing environment.”
The primary reason all of these approaches, including AI, fail to address the cybersecurity challenges of today is that they are not focused on survivability. As a result, they are reactive in nature. Survivability is not a new concept but a new term to denote resilience and fault tolerance, which have been concepts taught in computer science disciplines for years. However, similar to AI and machine learning, the community is now starting to adopt some of the principles as a more sustainable practice.
Cyber resilience refers to an entity’s ability to continuously deliver the intended outcome despite adverse cyber events. If there is a cyberattack, a system, network, application, or other technology medium should still perform as intended for the required amount of time to meet the required objective(s). Secondly, fault tolerance is the property that enables a system to continue operating properly if some (one or more faults within) of its components fail. In other words, failure (potentially due to a cyberattack) IS inevitable. However, fault tolerance ensures that the system will not stop operating properly.
CYBER SURVIVABILITY
As a result of these challenges, as well as the staggering statistics indicating we have not made much progress since the early Morris Worm attack, there is reason for alternative approaches that are more proactive in nature and scoped more appropriately. Cyber survivability takes the best of fault tolerant computing and resilience and attaches a mission focus to them by following these three simple principles:
- Assumes That Attacks Will Occur – hence, STARTS preparation with that assumption.
- Focuses on Mission – not concerned with attack prevention but on mission completion.
- Focuses on Preventing Actions on Objectives, Not Attacks – Step 7 of the cyber kill chain that enumerates the outcomes of a cyberattack—data theft, integrity attack, or denial of service.
It is helpful to understand the phases of a cyberattack to see how cyber survivability more effectively addresses cyberattack outcomes. The Cyber Kill Chain model was coined by Lockheed Martin [7] and enumerates the steps that attackers must go through to achieve their objective(s). It consists of the following seven steps:
- Reconnaissance – the observation stage: attackers typically assess the situation from the outside-in, in order to identify both targets and tactics for the attack.
- Weaponization – based on weaknesses determined in the reconnaissance phase, developing an exploit to take advantage of one or more of them.
- Delivery – delivering a malicious payload to the intended target.
- Exploitation – exploiting a vulnerability/weakness to execute malicious code on a victim’s machine.
- Installation – installing malware on the victim’s machine.
- Command and Control – communications and management channel for malware installed on victim’s machines and an adversary’s server.
- Actions on Objectives – accomplishing an adversary’s goals [8].
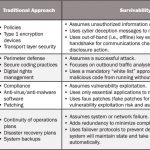
We define cyber survivability as the ability to remain mission capable after a cyberattack. Similar to traditional survivability, it can be further broken into four elements and subelements, as shown in Table 1.

CYBER SURVIVABILITY APPLICATIONS
Since survivability assumes attacks will occur, the Cyber Kill Chain “starts” operating when attackers try to achieve their actions on objectives. The three primary actions on objectives are denial of service, information theft, and deception attacks. Denial of service attacks deny service to legitimate users; information theft attacks steal information from legitimate users; and deception attacks deceive users into making decisions based on faulty information (e.g., phishing attacks).
Two validating mission goal examples for our new approach are as follows:
Mission Goal 1: establish secure communications channel to disseminate mission objectives between N number of military personnel. Assumes that communication will be breached; hence, it will establish a dynamic communications channel that will have the following properties:
- Cyber Deception: uses a mix of legitimate messages and deceptive messages. Adversary will have to distinguish between messages, even if communications channel is breached.
- Secure Sessions: tears down and reestablishes communications channel after each mission objective is received by military personnel. Adversary will have to breach EVERY channel after it is reestablished. They will also have to anticipate when a new channel is created.
- Mission Channels: set of communications channels only used during that mission (e.g., crypto keys) and destroyed after the mission. Adversary will have to breach each mission-based communication channel.
- Out-of-Band Keys (Optional): establishes pre-shared set of keys out of band prior to the mission—a primary and a backup in the event of an assumed breach. Adversary will have to determine the keys based on monitoring the communications channel, which will be encrypted with keys not established online.
Mission Goal 2: protect position location information (PLI) for ground control station for small unmanned aircraft system. Assumes that the ground control station will be stolen with PLI data; hence, it will leverage secure operating/file system properties to mitigate attack as follows:
- Secure Boot: will not allow the operating system to boot if the integrity appears to be compromised. Adversary will have to be able to access the system without modifying its integrity.
- Dual-Layer Encryption: uses both full disk (at the operating system level) and file system (at the file level) encryption to protect PLI data at rest. Adversary will have to break both disk AND file level encryption to access PLI data.
- Data Destruction: causes data corruption if ground control station is suspected to be compromised. Adversary will have to exploit the system without triggering the data destruction mechanism.
- Temporal Controls: PLI data will have a time-to-live (TTL) value that causes it to “expire” after a certain time. Adversary will have to exploit the system within the time period associated with the TTL.
Both of these examples follow the principles of cyber survivability by assuming that attacks will occur, focusing on mission objective, and maximizing an adversary’s ability to achieve their objective. In the first example, the objective of an adversary would be to successfully understand the traffic traversing the communications channel. This will be nearly impossible given the use of all the properties mentioned. In Mission Goal 2, an attacker’s goal would be to steal and access data resident on the Ground Control station. Similarly, the operating/file system properties proposed focus directly on mitigating that outcome as described. It is important to note that these properties, although potentially complementary to cybersecurity methods in place today, are very different in attempts to make it difficult for adversaries to accomplish their objectives within the context of a mission.
CONCLUSION
It is clear that new approaches to addressing the myriad of cybersecurity challenges are necessary. Concepts such as AI and its applications of machine learning and NLP serve as a step in the right direction to teach computers how to help us make sense of the volumes of data produced every day. However, given the statistics that demonstrate that cyberattacks are getting worse, we offer an alternative way to look at the problem of cyber defense and scope it based on mission objectives—cyber survivability.
Biography
Duane Wilson, a chief cybersecurity engineer with SURVICE Engineering Company, has been a practitioner in cybersecurity for almost 20 years. As a subject matter expert in cyber technology research, his areas of expertise include cybersecurity, business development, computer science engineering, and network protection. He provides subject matter expertise toward various cyber training and education initiatives through his consulting firm Wilson Innovative Solutions LLC, which provides innovative cyber research and development, advanced cybersecurity consulting, and cybersecurity training for all levels of experience in the commercial and federal sectors. Dr. Wilson holds a bachelor’s degree in computer science, a Master of Engineering in computer science from Cornell University, a second Master of Science in security informatics, and a Ph.D. in computer science from Johns Hopkins University.
References
- Ball, R. The Fundamentals of Aircraft Combat Survivability Analysis and Design, 2nd Edition. AIAA Education Series, pp. 2, 445, and 603, 2003.
- Federal Bureau of Investigation (FBI). “The Morris Worm: 30 Years Since First Major Attack on the Internet.” https://www.fbi.gov/news/stories/morris-worm-30-years-since-first-major-attack-on-internet-110218, 2 November 2018.
- Viruslist.com. “History of Malware: 1970s.” Kaspersky Lab, https://web.archive.org/web/20061016141708/http:/www.viruslist.com/en/viruses/encyclopedia?chapter=153310937, 16 October 2006.
- Symantec Corporation. “10 Cyber Security Facts and Statistics for 2018.” Norton, https://us.norton.com/internetsecurity-emerging-threats-10-facts-about-todays-cybersecurity-landscape-that-you-should-know.html, accessed April 2019.
- (ISC)², Inc. “Cybersecurity Workforce Study, 2018.” https://www.isc2.org/Research/Workforce-Study#, accessed April 2019.
- Recorded Future Team. “Machine Learning: Practical Applications for Cybersecurity.” Recorded Future Blog, https://www.recordedfuture.com/machine-learning-cybersecurity-applications/, 14 March 2018.
- Lockheed Martin. “The Cyber Kill Chain.” https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html, accessed April 2019.
- Hospelhorn, S. “What Is the Cyber Kill Chain and How to Use It Effectively.” Varonis, https://www.varonis.com/blog/cyber-kill-chain/, 7 December 2018.